使用的固件
Kiddin‘ 的Generic x86/64固件,https://supes.top/。
DNS链路
Bypass开启AdGuardHome联动的情况下,全链路为AdGuardHome->DNSMASQ->ChinaDNS-NG->SmartDNS,
SmartDNS是本地的最上游DNS服务器,再往上就是公共的DNS了。
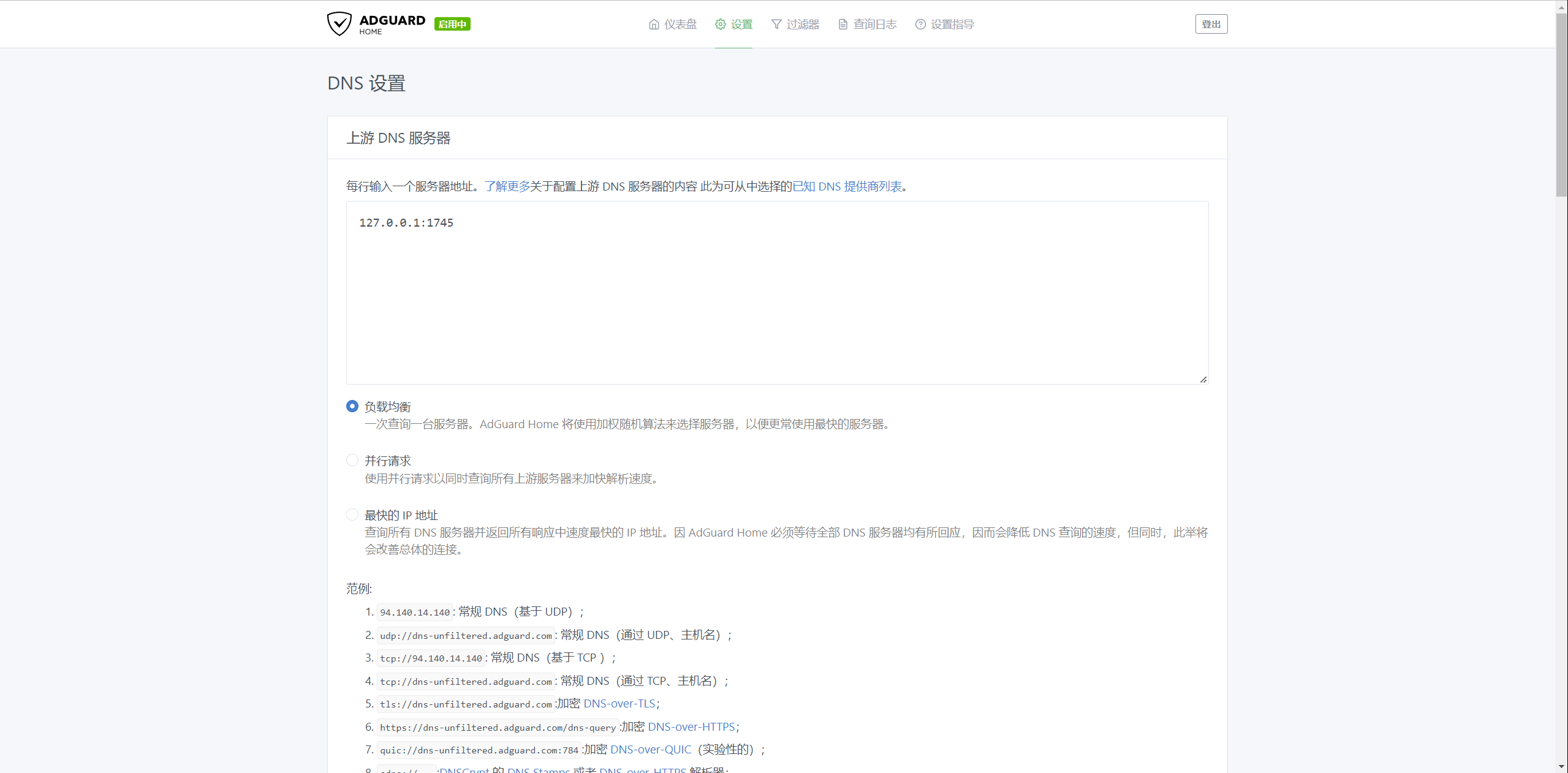
AdGuard Home
客户端发送DNS解析请求,首先从AdGuardHome出发,转发到1745端口
Dnsmasq
1745端口为Dnsmasq服务的端口,我们看一下正在运行的Dnsmasq进程
root@OpenWrt 06:42 PM /# ps | grep dns
1380 dnsmasq 3524 S /usr/sbin/dnsmasq -C /var/etc/dnsmasq.conf.cfg01411c -k -x /var/run/dnsmasq/dnsmasq.cfg01411c.pid
12925 root 1180 R grep dns
15340 root 7572 S /usr/sbin/smartdns -c /var/etc/smartdns/smartdns.conf
15354 root 1208 S /usr/bin/chinadns-ng -l 5337 -c 127.0.0.1#5336 -t 127.0.0.1#5335 -4 china_v4 -6 china_v6 -f -n -g /etc/bypass/gfw.list
配置文件为/var/etc/dnsmasq.conf.cfg01411c,内容如下,可以看到port设置为1745
root@OpenWrt 06:49 PM dnsmasq.d# cat /var/etc/dnsmasq.conf.cfg01411c
# auto-generated config file from /etc/config/dhcp
conf-file=/etc/dnsmasq.conf
dhcp-authoritative
domain-needed
localise-queries
read-ethers
enable-ubus=dnsmasq
expand-hosts
bind-dynamic
all-servers
cache-size=8192
dns-forward-max=8192
port=1745
edns-packet-max=1232
domain=lan
local=/lan/
addn-hosts=/tmp/hosts
dhcp-leasefile=/tmp/dhcp.leases
resolv-file=/tmp/resolv.conf.d/resolv.conf.auto
dhcp-broadcast=tag:needs-broadcast
conf-dir=/tmp/dnsmasq.d
user=dnsmasq
group=dnsmasq
dhcp-ignore-names=tag:dhcp_bogus_hostname
conf-file=/usr/share/dnsmasq/dhcpbogushostname.conf
bogus-priv
conf-file=/usr/share/dnsmasq/rfc6761.conf
no-dhcp-interface=br-lan
有conf-file和conf-dir两个参数
root@OpenWrt 10:07 PM ~# cat /etc/dnsmasq.conf
# Change the following lines if you want dnsmasq to serve SRV
# records.
# You may add multiple srv-host lines.
# The fields are <name>,<target>,<port>,<priority>,<weight>
# A SRV record sending LDAP for the example.com domain to
# ldapserver.example.com port 289
#srv-host=_ldap._tcp.example.com,ldapserver.example.com,389
# Two SRV records for LDAP, each with different priorities
#srv-host=_ldap._tcp.example.com,ldapserver.example.com,389,1
#srv-host=_ldap._tcp.example.com,ldapserver.example.com,389,2
# A SRV record indicating that there is no LDAP server for the domain
# example.com
#srv-host=_ldap._tcp.example.com
# The following line shows how to make dnsmasq serve an arbitrary PTR
# record. This is useful for DNS-SD.
# The fields are <name>,<target>
#ptr-record=_http._tcp.dns-sd-services,"New Employee Page._http._tcp.dns-sd-services"
# Change the following lines to enable dnsmasq to serve TXT records.
# These are used for things like SPF and zeroconf.
# The fields are <name>,<text>,<text>...
#Example SPF.
#txt-record=example.com,"v=spf1 a -all"
#Example zeroconf
#txt-record=_http._tcp.example.com,name=value,paper=A4
# Provide an alias for a "local" DNS name. Note that this _only_ works
# for targets which are names from DHCP or /etc/hosts. Give host
# "bert" another name, bertrand
# The fields are <cname>,<target>
#cname=bertand,bert
log-facility=/dev/null
conf-dir=/etc/dnsmasq.d
先看/etc/dnsmasq.conf
基本都是自动生成的注释,最后一行又指定了一个conf-dir
root@OpenWrt 10:09 PM ~# ls /etc/dnsmasq.d
bogus-nxdomain.china.conf
里面有一个bogus-nxdomain.china.conf,内容:
## Public DNS
# DNSPai
bogus-nxdomain=123.125.81.12
bogus-nxdomain=101.226.10.8
# Level3
bogus-nxdomain=198.105.254.11
bogus-nxdomain=104.239.213.7
## China Telecom
# Anhui Telecom
bogus-nxdomain=61.191.206.4
# Beijing Telecom
bogus-nxdomain=218.30.64.194
# Chengdu Telecom
bogus-nxdomain=61.139.8.101
bogus-nxdomain=61.139.8.102
bogus-nxdomain=61.139.8.103
bogus-nxdomain=61.139.8.104
# Fujian Telecom
bogus-nxdomain=42.123.125.237
# Gansu Telecom
bogus-nxdomain=202.100.68.117
# Guangxi Telecom
bogus-nxdomain=113.12.83.4
bogus-nxdomain=113.12.83.5
# Hainan Telecom
bogus-nxdomain=202.100.220.54
# Hangzhou Telecom
bogus-nxdomain=60.191.124.236
bogus-nxdomain=60.191.124.252
# Hebei Telecom
bogus-nxdomain=222.221.5.204
# Hunan Telecom
bogus-nxdomain=124.232.132.94
# Jiangsu Telecom
bogus-nxdomain=202.102.110.204
......
这里面是一些已知的,会进行DNS劫持的DNS(在这里找到的https://github.com/felixonmars/dnsmasq-china-list)
bogus-nxdomain.china.conf: Known addresses that are hijacking NXDOMAIN results returned by DNS servers.
NXDOMAIN指的是不存在的域名,当DNS收到一个不存在域名的解析请求,就会出现NXDOMAIN:
Host abcquq12examfooltest.com not found: 3(NXDOMAIN)
bogus-nxdomain.china.conf里的DNS在解析到不存在域名时,会展示广告或者别的网址,所以叫DNS劫持。
再看/tmp/dnsmasq.d
里面也有一个配置文件,将DNS请求转发到5337端口
root@OpenWrt 10:20 PM dnsmasq.d# cat dnsmasq-by.conf
no-resolv
server=127.0.0.1#5337
conf-dir=/tmp/dnsmasq.by
然后又指向了一个配置文件夹,里面的内容:
root@OpenWrt 10:20 PM dnsmasq.d# ls /tmp/dnsmasq.by
black.conf white.conf
里面的内容:
root@OpenWrt 10:22 PM dnsmasq.by# cat black.conf
server=/api.ipify.org/127.0.0.1#5335
server=/ecchi.iwara.tv/127.0.0.1#5335
server=/githubusercontent.com/127.0.0.1#5335
server=/iwara.tv/127.0.0.1#5335
server=/raw.githubusercontent.com/127.0.0.1#5335
server=/test-ipv6.com/127.0.0.1#5335
server=/whrq.net/127.0.0.1#5335
root@OpenWrt 10:22 PM dnsmasq.by# cat white.conf
server=/checkip.dyndns.org/127.0.0.1#5336
server=/checkipv6.dyndns.org/127.0.0.1#5336
server=/checkip.synology.com/127.0.0.1#5336
server=/op.supes.top/127.0.0.1#5336
对应着Bypass里面的不走代理的域名和强制走代理的域名
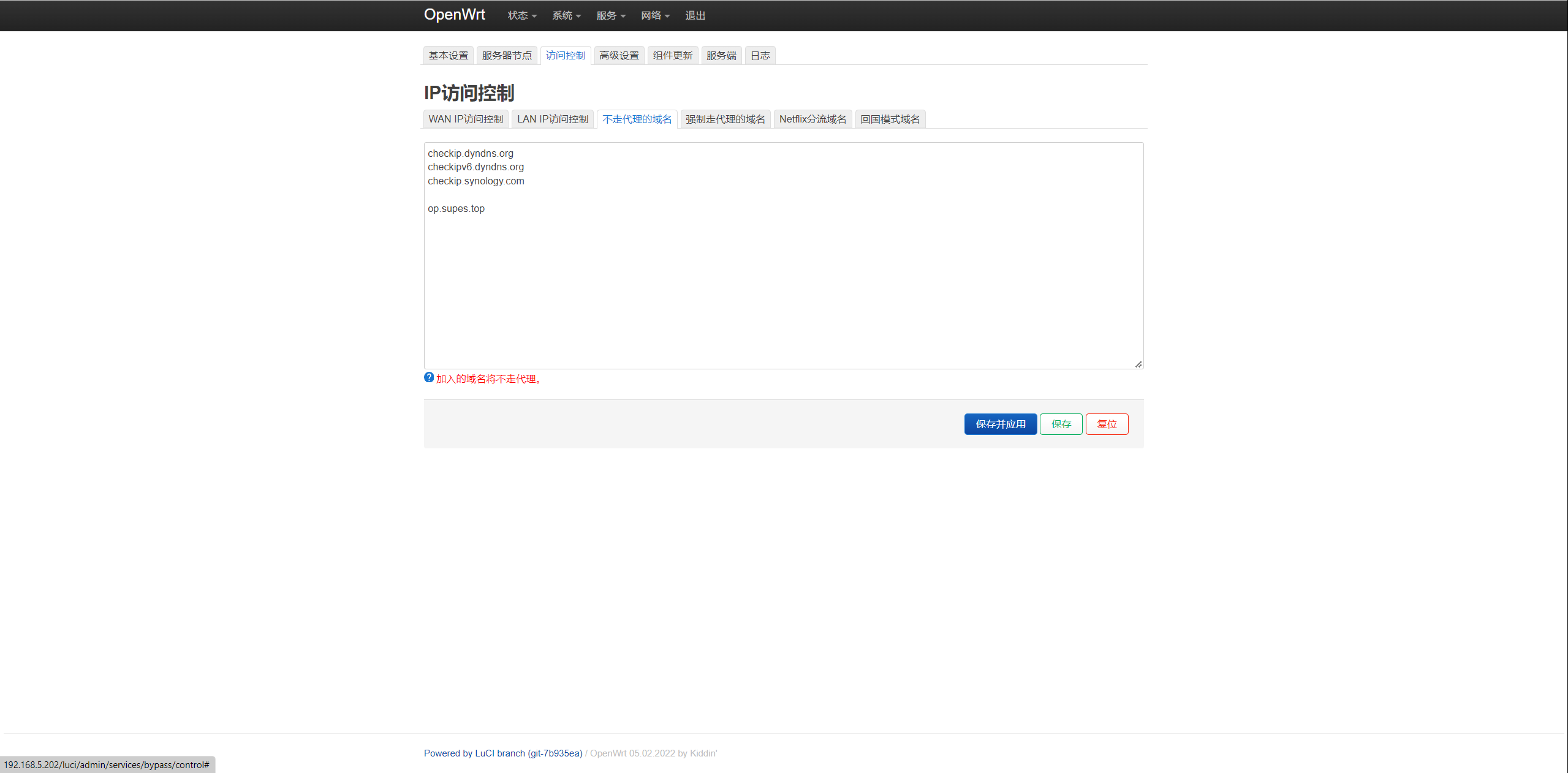
ChinaDNS-NG
ChinaDNS-NG监听端口5337,
root@OpenWrt 10:22 PM dnsmasq.by# ps | grep dns
1380 dnsmasq 3564 S /usr/sbin/dnsmasq -C /var/etc/dnsmasq.conf.cfg01411c -k -x /var/run/dnsmasq/dnsmasq.cfg01411c.pid
8087 root 1180 R grep dns
15340 root 7572 S /usr/sbin/smartdns -c /var/etc/smartdns/smartdns.conf
15354 root 1208 S /usr/bin/chinadns-ng -l 5337 -c 127.0.0.1#5336 -t 127.0.0.1#5335 -4 china_v4 -6 china_v6 -f -n -g /etc/bypass/gfw.list
参数解释 from https://github.com/zfl9/chinadns-ng,-c为国内DNS,-t为国外DNS
$ chinadns-ng --help
usage: chinadns-ng <options...>. the existing options are as follows:
-b, --bind-addr <ip-address> listen address, default: 127.0.0.1
-l, --bind-port <port-number> listen port number, default: 65353
-c, --china-dns <ip[#port],...> china dns server, default: <114DNS>
-t, --trust-dns <ip[#port],...> trust dns server, default: <GoogleDNS>
-4, --ipset-name4 <ipv4-setname> ipset ipv4 set name, default: chnroute
-6, --ipset-name6 <ipv6-setname> ipset ipv6 set name, default: chnroute6
-g, --gfwlist-file <file-path> filepath of gfwlist, '-' indicate stdin
-m, --chnlist-file <file-path> filepath of chnlist, '-' indicate stdin
-o, --timeout-sec <query-timeout> timeout of the upstream dns, default: 5
-p, --repeat-times <repeat-times> it is only used for trustdns, default: 1
-M, --chnlist-first match chnlist first, default: <disabled>
-N, --no-ipv6 disable ipv6-address query (qtype: AAAA)
-f, --fair-mode enable `fair` mode, default: <fast-mode>
-r, --reuse-port enable SO_REUSEPORT, default: <disabled>
-n, --noip-as-chnip accept reply without ipaddr (A/AAAA query)
-v, --verbose print the verbose log, default: <disabled>
-V, --version print `chinadns-ng` version number and exit
-h, --help print `chinadns-ng` help information and exit
bug report: https://github.com/zfl9/chinadns-ng. email: zfl9.com@gmail.com (Otokaze)
SmartDNS
SmartDNS负责对分流过后的域名进行分组,交给不同的上游DNS解析。国内的域名交给国内的DNS,国外的域名交给国外的DNS。
从配置文件里可以看到,分为了 a/b 和 e/f 两组,分别对应国外和国内。
force-AAAA-SOA yes
speed-check-mode none
dualstack-ip-selection yes
cache-size 0
cache-persist no
log-level fatal
log-file /var/log/bypass.log
bind :5335 -group a
bind :5336 -group e -no-rule-soa
server-https https://dns.google/dns-query -group a -exclude-default-group
server-tcp 8.8.8.8 -group b -exclude-default-group
server-tcp 8.8.4.4 -group b -exclude-default-group
nameserver /dns.google/b
server-https https://dns.alidns.com/dns-query -group e -exclude-default-group
server 223.5.5.5 -group f -exclude-default-group
server 223.6.6.6 -group f -exclude-default-group
server 2400:3200::1 -group f -exclude-default-group
server 2400:3200:baba::1 -group f -exclude-default-group
domain-rules /dns.alidns.com/ -nameserver f -ipset ss_spec_wan_ac
conf-file /var/etc/smartdns/rules.conf
国外选a还是b,国内选e还是f,选择根据Bypass中的配置而定
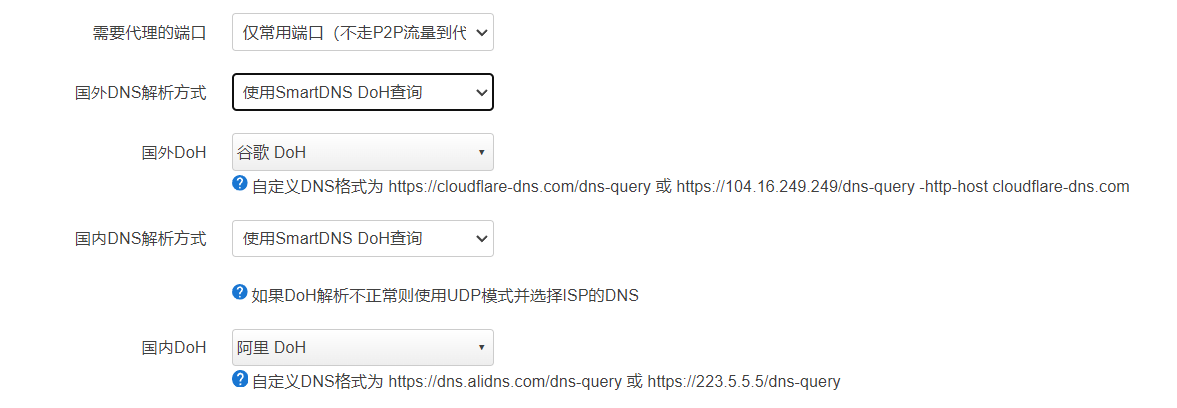
到这里,本地DNS分流就结束了,后面交给公共DNS解析出真正的IP。


评论区